Laiye Chatbot checks for existence and validity of the X-Mindsay-Signature HTTP header in order to validate request authenticity. In order to do so, Laiye Chatbot and its partner share a secret key (set up during the integration).
Laiye Chatbot partner must generate a signature when requesting the API. Laiye API tries to generate the same signature on its side and checks that it matches the signature given in X-Mindsay-Signature HTTP header.
To prevent replay attacks, Laiye API also validates that the X-Mindsay-Timestamp is not too far in the past (5 minutes tolerance).
Here is the way to generate the signature:
- Concatenate the value in
X-Mindsay-Timestampheader with the request body - Compute the hexadecimal hash of this string by using standard
HMAC-SHA256algorithm and the shared secret key
Example
X-Mindsay-Timestamp:
1575215418
Body:
{"unique_chatter_identifier_key": "member_id", "unique_chatter_identifier_value": "123"}
Secret:
a_secure_secret
Concatenated value:
1575215418{"unique_chatter_identifier_key": "member_id", "unique_chatter_identifier_value": "123"}
Computed HMAC:
acee24dc55838d04dbd879967dffda464f843799a9e6b14c97d9a2b908de6d85
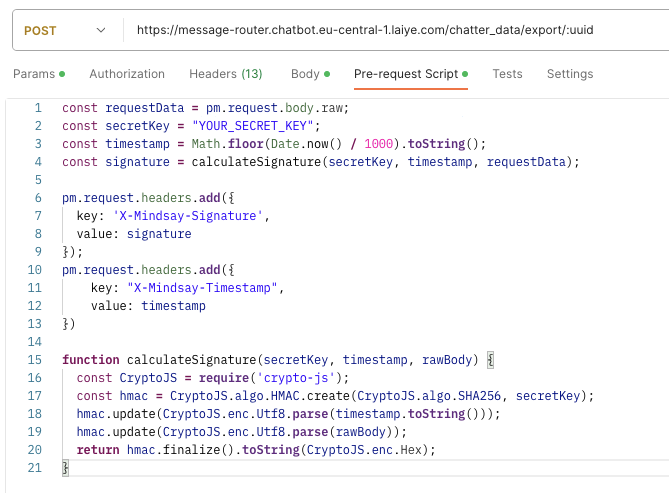
This can be generated as follows:
const requestData = pm.request.body.raw;
const secretKey = "your-secret-key";
const timestamp = Math.floor(Date.now() / 1000).toString();
const signature = calculateSignature(secretKey, timestamp, requestData);
pm.request.headers.add({
key: 'X-Mindsay-Signature',
value: signature
});
pm.request.headers.add({
key: "X-Mindsay-Timestamp",
value: timestamp
})
function calculateSignature(secretKey, timestamp, rawBody) {
const CryptoJS = require('crypto-js');
const hmac = CryptoJS.algo.HMAC.create(CryptoJS.algo.SHA256, secretKey);
hmac.update(CryptoJS.enc.Utf8.parse(timestamp.toString()));
hmac.update(CryptoJS.enc.Utf8.parse(rawBody));
return hmac.finalize().toString(CryptoJS.enc.Hex);
You can copy & paste this snippet into a Postman request as a Pre-request script